Introduction
This guide provides a comprehensive walkthrough of a forensic investigation into a potential infection of an Android device, received by a civic society organization that operates as a helpline for individuals at risk. The focus is on consensual forensics, emphasizing a respectful, do-no-harm approach based on the unique challenges in this field. This guide takes an exploratory approach, given the limited tools and methodologies available for consensual forensics within the CSO context. While there are notable open-source resources created and maintained by trusted organizations and communities, they are limited compared to those in the law enforcement -non-consensual- forensic field.
This five-part guide covers the entire process from initial case reception and triage to in-depth technical forensic analysis, focusing on identifying traces of infection and analyzing the behavior of a malicious app. It concludes with guidance on cleaning the infected device and summarizing the findings. In this specific case, we simulate an infection caused by a malicious app, known as “TheTruthSpy,” which is recognized for its use as stalkerware in facilitating gender-based digital violence.
The helpline example assumes a holistic approach to supporting individuals at risk, backed by an interdisciplinary team. While the guide focuses on technical aspects, it acknowledges the critical role of holistic support. Communication with the person at risk is ongoing throughout the process, even though this is not explicitly detailed for clarity in this guide.
The guide is structured into five parts, each illustrating a different phase of case handling by the helpline:
Part 1 (This page)
- Case reception: the helpline receives a message from a person concerned that her ex-partner is persistently accessing private information from her conversations, even though they have been separated for some time. A vetting process is conducted to verify the identity of the person and ensure the legitimacy of the case before it is accepted.
- Contextual information: while assessing the need for and providing holistic support to the person, an interview is conducted to ask key questions and gather relevant background information.
- Initial triage: the triaging team of the helpline assesses the potentially compromised device using its graphical interface. For the purposes of this guide, we assume the helpline has physical access to the device; however, every step outlined can also be performed remotely if necessary. If any suspicious signs are identified, the team proceeds to a detailed forensic analysis.
- Forensic analysis: the case is passed to the technologists of the helpline, who use a forensic workstation to acquire and analyze data from the phone for signs of compromise. As an ongoing infection with a malicious app is detected, they move on to an in-depth app analysis.
- App analysis: the technologists download the malicious app from the infected device, and conduct both static analysis (reviewing the app’s code) and dynamic analysis (observing its behavior and traffic) to understand its capabilities.
- Closing remarks: they provide guidance on cleaning the device to the owner and -only for the purposes of this guide- offer a summary on the case.
Part 1: Starting a case and preliminary triage
1. Contextual information:
Before conducting any technical analysis, it is crucial for the helpline to first provide initial support that focuses on the emotional and psychological state of the person at risk. This includes assessing the severity of the incident and engaging in active listening to ensure the individual feels heard and supported. This
holistic approach ensures that the technical aspects of the case are managed in a way that prioritizes the individual’s overall safety and well-being (Vita Activa, 2022).
While assessing the need for and providing holistic support, the helpline conducts an interview to ask key questions and gather relevant background information.
Brief selection of questions & answers from the interview:
The information gathered as answers to these questions will be useful in the following stages of the analysis.
1. What raised your suspicions that something was wrong with your mobile device?
According to the owner of the device:
- The battery drains very quickly.
- The person suspects that her ex-partner has done something to her phone, as he seems to have access to private conversations held on her phone.
2. Can you provide a timeframe for when this happened?
There isn’t a specific timeframe; the harassment has been ongoing for several months.
3. Did anyone have physical access to the device?
Yes, the ex-partner had physical access to the device and knows its PIN code.
4. Have you made any changes to the phone recently (such as uninstalling apps, wiping it)?
No
5. Do you have a spare phone to use during the analysis?
Yes
6. What are your expectations after the analysis?
According to the owner of the device:
- Understand how private conversations where compromise
- Ensure the device is secure and free of any infection.
Based on the interview we can assume the attacker had had pyshycal access to the phone and also is aware of the PIN code. With this contextual information in mind, we build our intuition of what to look for in the next phases of the case.
2. Initial triage
Side-by-side with the person-at-risk we perform a walkthrough of the mobile device’s graphical interface to check for signs of compromise.
Throughout the entire preliminary triage process, the person conducting the assessment will ensure that the owner of the phone feels comfortable and in control. We will walkthrough the phone’s settings together, clearly explaining each step in simple terms, without using any technical jargon. The person at risk will be encouraged to ask questions, and we will explain what we’re looking for in a way that helps them understand and possibly identify issues on their own in the future. Importantly, at every stage, the owner of the device will be reminded that they have the right to opt out or pause the process at any time.
Their written consent will be obtained before proceeding with this phase.
The following settings, options and menus were checked for signs of compromise during the initial triage of the phone via the graphic interface. Bare in mind that this triage was tested on a Motorola G20 model, but menu options may vary by device and vendor.
a. Review apps requesting sensitive permissions
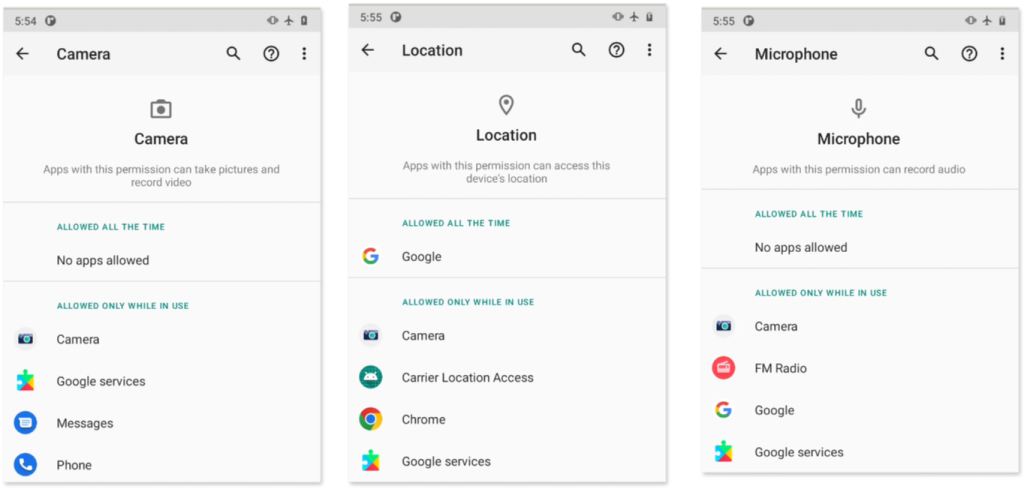
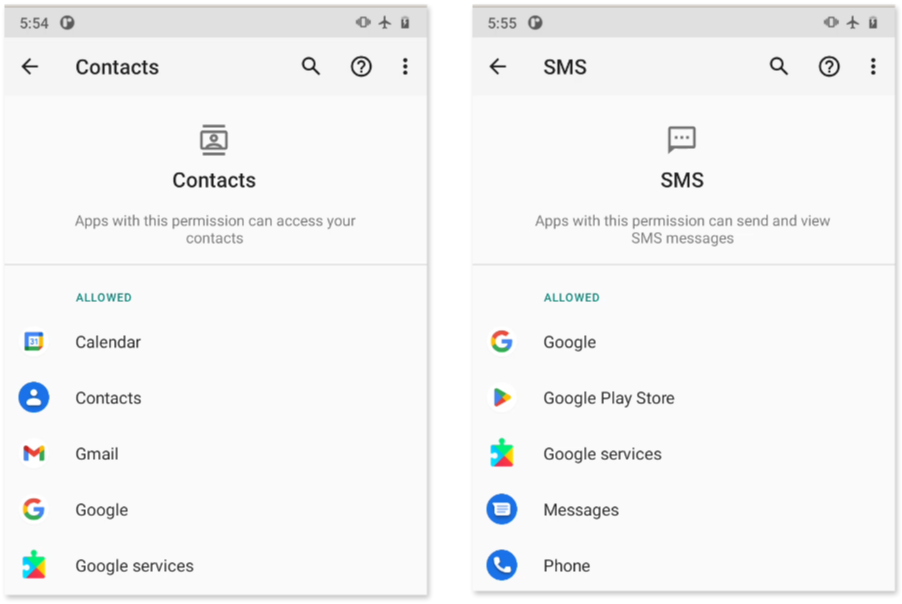
Android’s permission system controls access to sensitive capabilities on a device, such as sending SMS messages or accessing private information like Contacts information. It is important to review any apps that have access to sensitive permissions, including location, camera, microphone, and SMS, among others.
When evaluating apps with dangerous permissions, consider having in mind these key questions:
- Is the permission relevant to the app’s functionality? For example, why would a calculator app need access to your contacts?
- Does an app repeatedly request multiple dangerous permissions? Be wary of apps that seek access to several critical functions without a clear need.
- Is the app a system app or a user-installed app? This distinction can help determine the app being trustworthy.
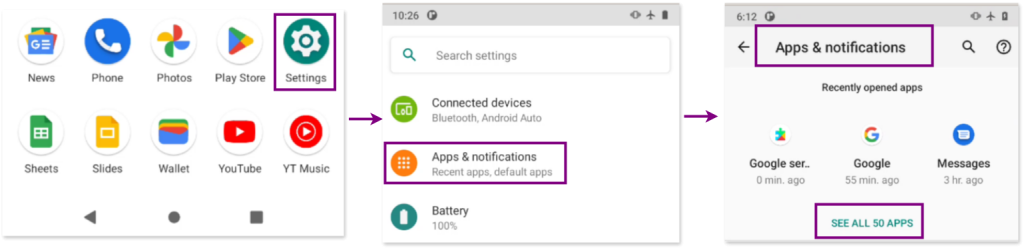
To review these permissions, navigate to: Settings > Apps & Notifications > Permission Manager
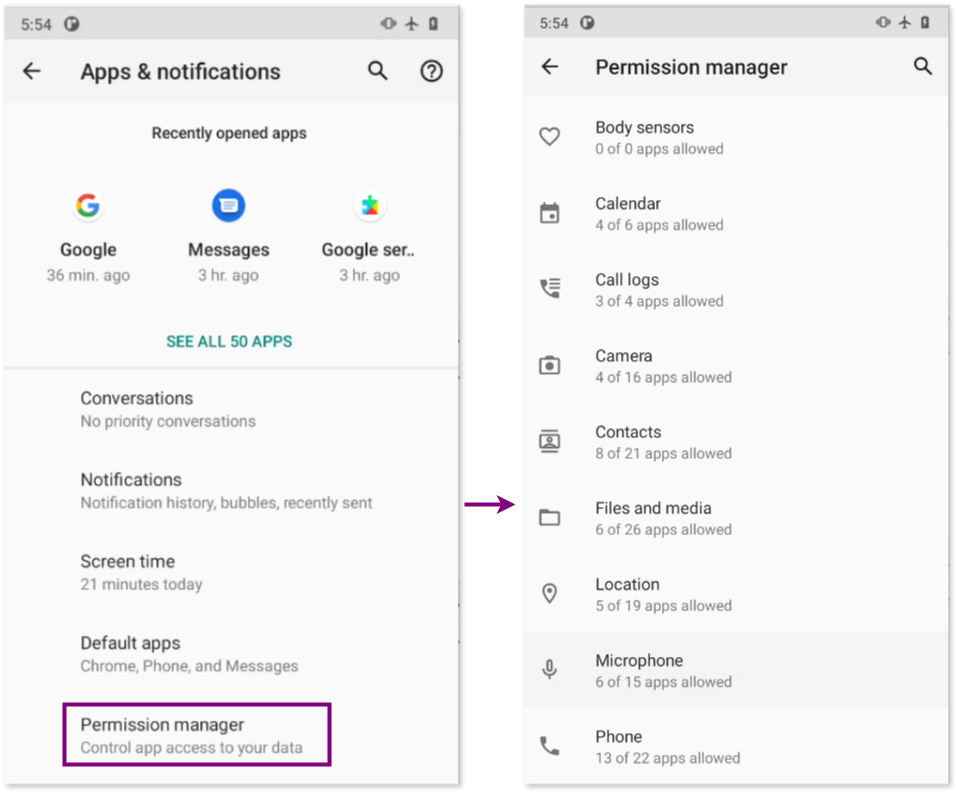
Dangerous permissions: examine the apps that have been granted access to permissions like Camera, Contacts, Location, and Microphone, as well as others that catch your attention.
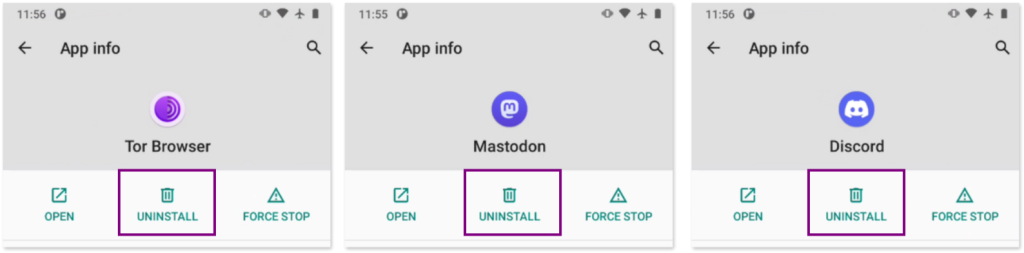
Distinguishing system apps from user-installed apps: to determine whether an app is a system app or one installed by a user (or potentially by an attacker), go to the App Info Menu in Settings > Apps & Notifications > See all apps. System apps or apps that come pre-installed by the manufacturer of the phone, usually have limited uninstallation options and are typically more trustworthy. They have the option to disable them but not to uninstall them. In contrast, user-installed apps (or those potentially installed by an attacker) often have the option to uninstall them.
It’s important to note that the ability to uninstall an app is not always an indication that it’s a user-installed app; some pre-installed apps can also be uninstalled. However, this can still be a useful factor in building intuition around whether an app might be malicious or not, especially when combined with other indicators like permissions, source of installation, and the app’s behavior.
To review the App Info Menu, navigate to:
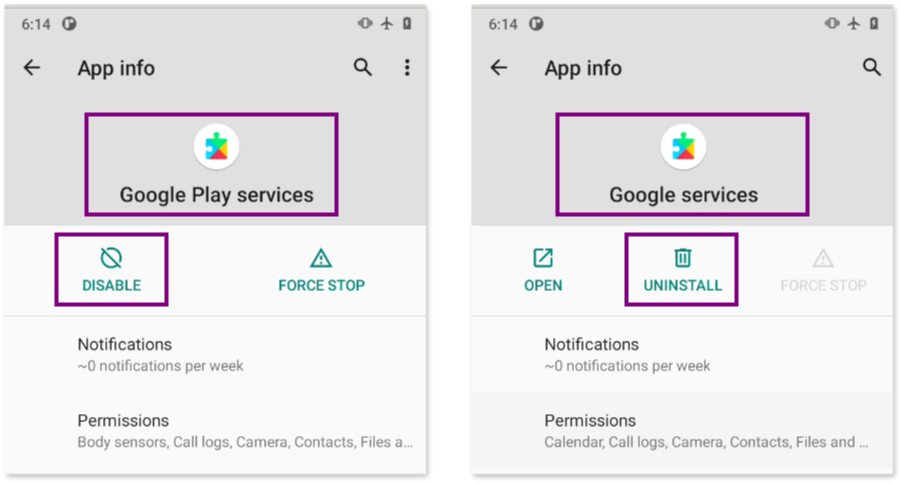
Apps that come pre-installed with the phone and cannot be uninstalled only show the option to “Disable”:

Apps installed by the user show the “Uninstall” option:
b. Special app access
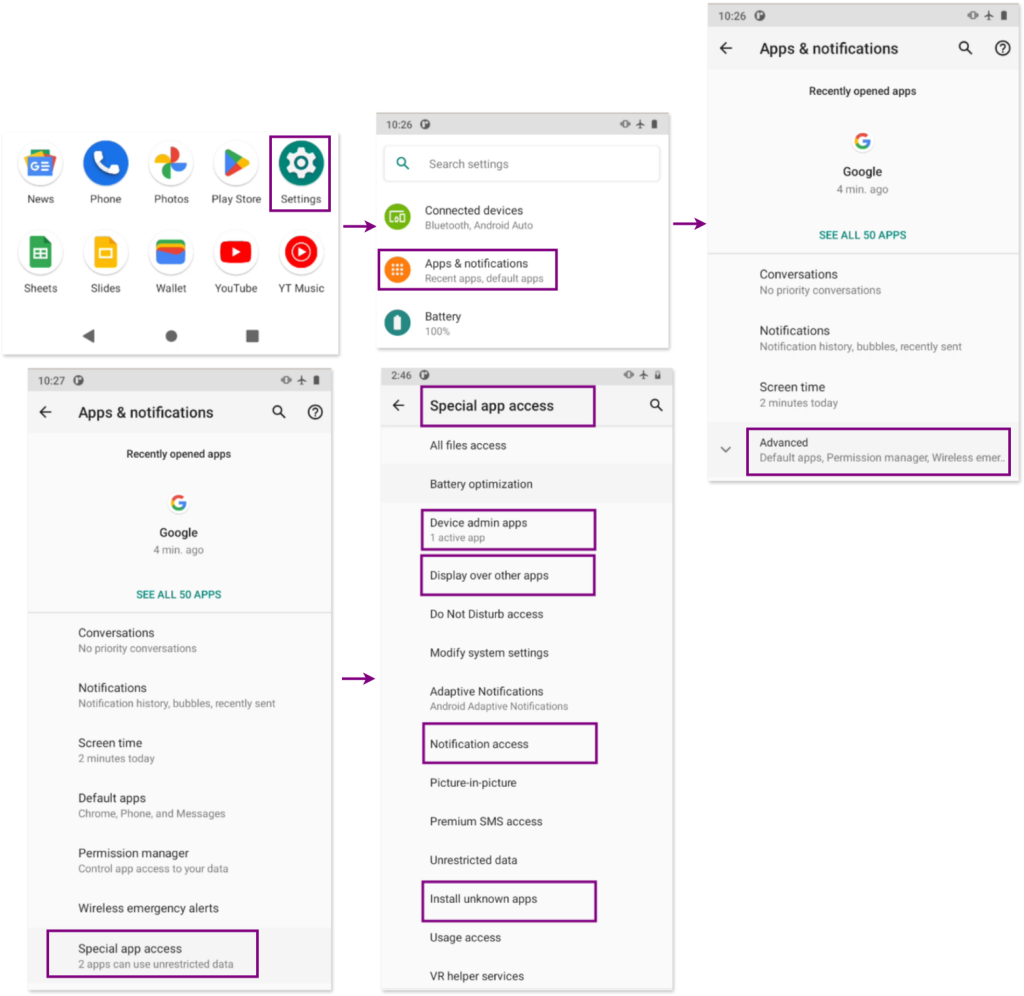
This refers to specific access that allow apps to perform actions beyond standard permissions.
Key options to review in the Special app access Menu are:
- Device admin apps: verify if any app have administrator rights.
- Display over other apps: check if any app can display content over other apps, which could be used maliciously.
- Notification access: verify which apps can manage and read your notifications.
- Install unknown apps: review which apps can install other apps from outside the Play Store. Malicious applications are often excluded from the Google Play Store due to their malicious nature and need to be installed by other means (such as via the browser).
To review these special access, go to: Settings > Apps & Notifications > Special app access:
c. Apps subscribed to Accessibility services
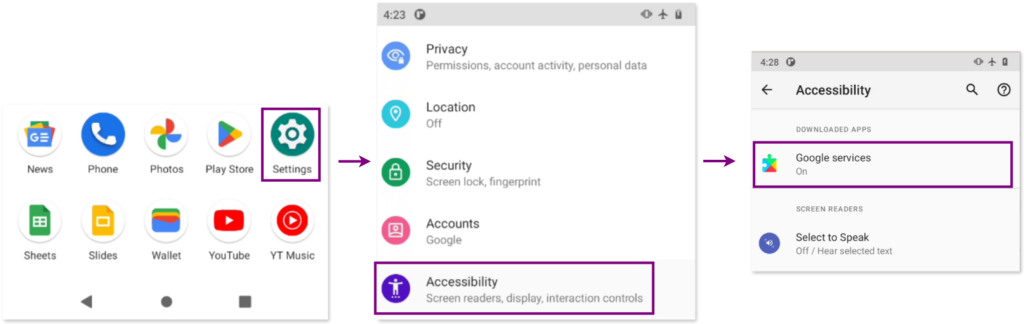
Accessibility services in Android are designed to assist users with disabilities by providing apps the ability to interact with the device on a deeper level. However, when misused, these services can give an app extensive control over the device, enabling it to monitor and log user actions or read screen content.
To find out which apps are subscribed to Accessibility Services, go to: Settings > Accessibility:
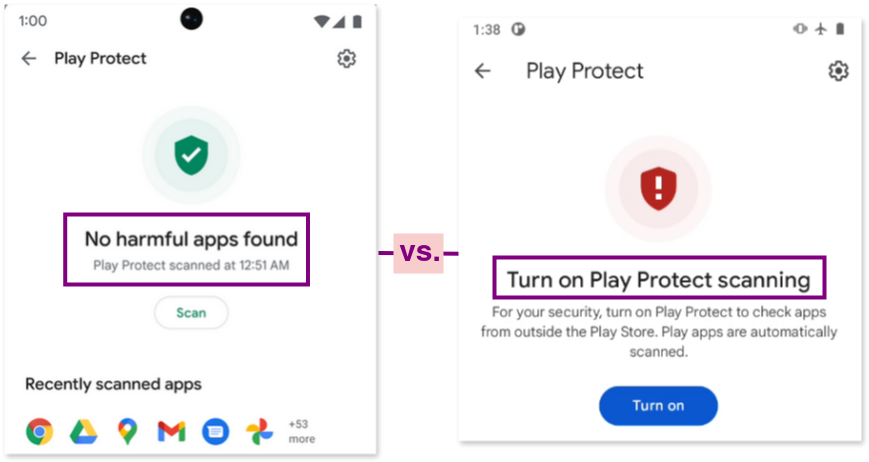
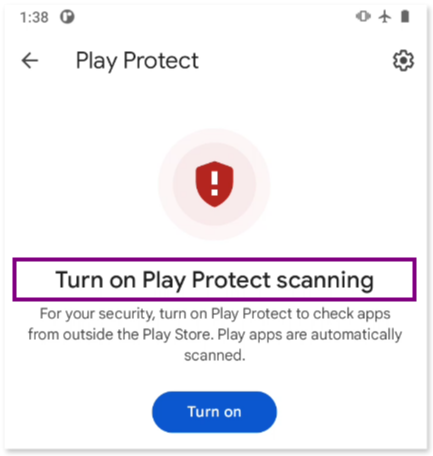
d. Google Play Protection
Google Play Protect is an antivirus-like service on Android phones that scans and blocks malicious apps, especially those installed from outside the Google Play Store. However, it can be disabled, which allows malicious apps to bypass these protections. Many harmful apps include instructions to disable Play Protect to avoid detection.
To check if Google Play Protect is enabled, open the Google Play App, tap on the profile icon, and then select the “Play Protect” menu.
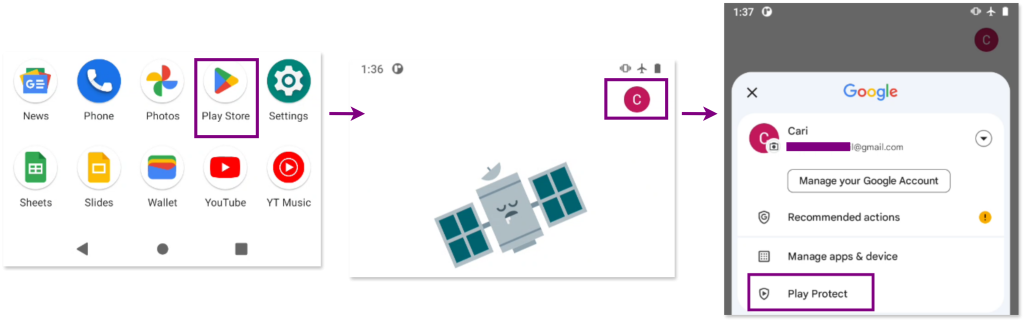
Whether Google Play Protect is enabled (left image) or disabled (rigth image), you will see a message similar to this:
e. Google Account Settings
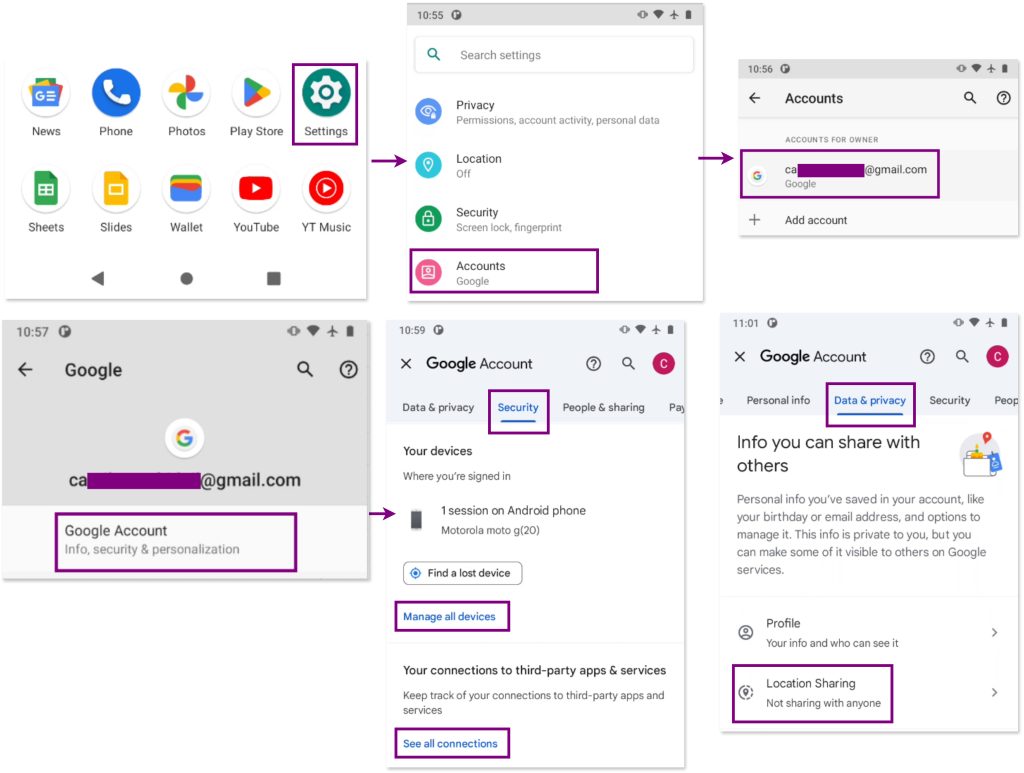
From the device, you can review the security of the Google account linked to the mobile device. This includes checking the account Settings to ensure there are no unfamiliar devices or third-party services connected to the account, which could indicate unauthorized access. Additionally, review the shared location settings to verify that location information isn’t being shared with unknown or unintended parties. This step helps identify potential compromises in account security.
To check the Google Account settings go to: Settings > Accounts > Google account > Security / Data & Privacy Menues.
Findings of a potential infection
After reviewing all the menus and options mentioned earlier, these were the findings that raise suspicions from the triager of the helpline and suggest a potential infection on the device.
Suspicious duplication of apps
After reviewing apps with Special app access in Settings > Apps & Notifications > Special app access, we identified two apps that raised concerns as shown in the following picture:
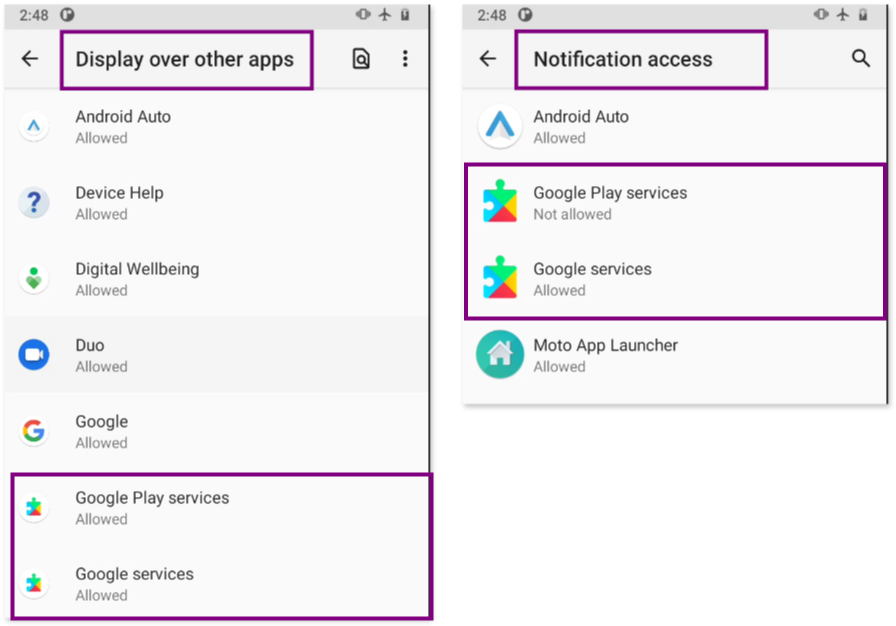
These apps appear to be duplicates of each other, having a very similar name and an identical icon.
Sensitive permissions being requested
One of those two apps, the one named “Google Services,” was repeatedly found in the Permission Manager (in Settings > Apps & Notifications > Permission Manager), requesting and holding permissions for the Camera, Location, Microphone, Contacts and SMS.
Accessibility and Device admin
That same app, “Google Services”, also requested (and granted with) Device Administration privileges (in Settings > Apps & Notifications > Special app access) and binded to Accessibility services (in Settings > Accessibility).
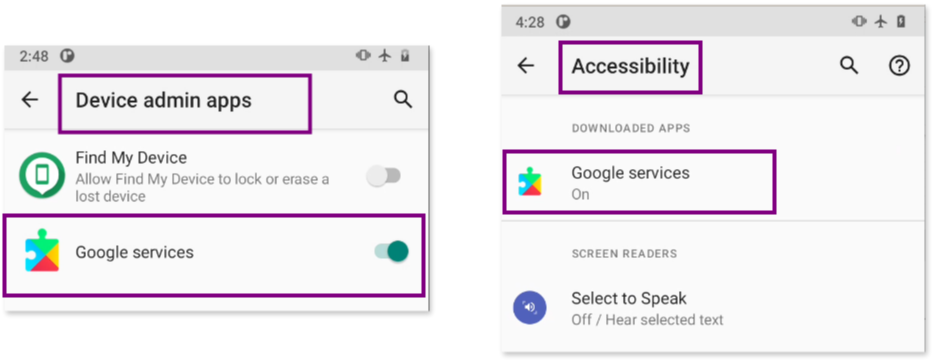
At this point, we have identified two apps that seem nearly identical -with very similar names and icons- but one is requesting more permissions than the other. Although we’re still uncertain about their nature, the app consistently present across all the settings we checked raises our suspicions.
System app vs user installed app
To determine which of these apps is a system app and which, if any, was installed by the user (recalling that the attacker had physical access to the phone), we examined the App Info menu in Settings > Apps & Notifications > App info. Here, we can view details about each app, including permissions and whether they can be disabled or uninstalled.
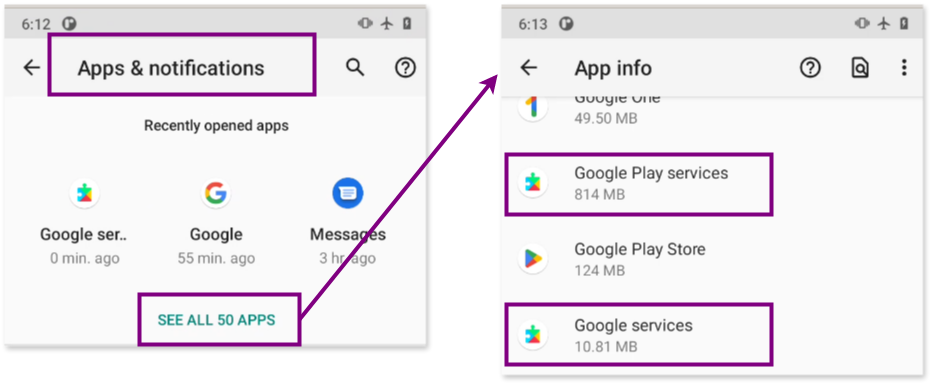
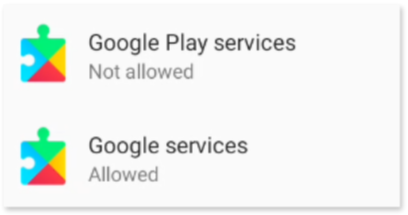
When examining both apps, we notice that “Google services” can be uninstalled, which suggests it’s not a system app, while “Google Play services” can only be disabled, confirming it as a system app.
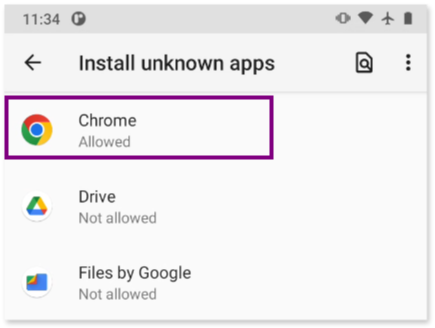
Apps installed from untrusted sources
We also discovered that apps can be installed on the phone from outside the Google Play Store. The Chrome browser was granted permission to install apps when we reviewed the Install unknown app Menu (in Settings > Apps & Notifications > Special app access). This means that if there are any malicious app installed in the phone, not present in the Play Store due to its harmful nature, it could have been installed via the browser visiting a webpage.
Insecure state of the phone
Finally, when we opened the Google Play App, tapped on the profile icon, and then selected the “Play Protect” menu, we found that Google Play Protect was disabled. This implies that the phone in an insecure and potentially vulnerable state.
Conclusion
This section aimed to demonstrate the value of conducting an initial non-technical triage of a potentially infected device to assess the likelihood of an infection. For this specific case, through this initial triage via the device’s graphical interface, we were able to flag an application as potentially suspicious. We will now proceed to a more technical forensic analysis to further investigate any signs of compromise.
It is important to note before heading to the next forensic phase, that the escalation of the case from triage using the graphic interface of the device to a technical forensic analysis depends on various factors, such as the technical capabilities within the team (or the need to collaborate with technical experts from outside the organizations), the urgency of the case and the objectives of the investigation, which may require to clean the device immediately after triage or rely on, for example, a different type of forensic experts able to gather evidence suitable for legal proceedings.
This guide was created by tes and is shared under Creative Commons BY-NC-SA license; for any errors or enhancements, please share your feedback via email (`[email protected]`) or keybase (`https://keybase.io/texturas`)